The Essential Guide to Cybersecurity for SMBs
Why Cybersecurity Matters for SMBs
Cybersecurity isn't just for major corporations anymore. Small and medium-sized businesses (SMBs) are increasingly targeted by cybercriminals due to:
- Richer Data: You manage valuable data like customer PII, PHI, intellectual property, and financial records.
- Perceived Vulnerability: The lack of a robust cybersecurity program makes SMBs easier targets.
- Limited Resources: SMBs often lack in-house cybersecurity expertise and bandwidth.
The Growing Threat:
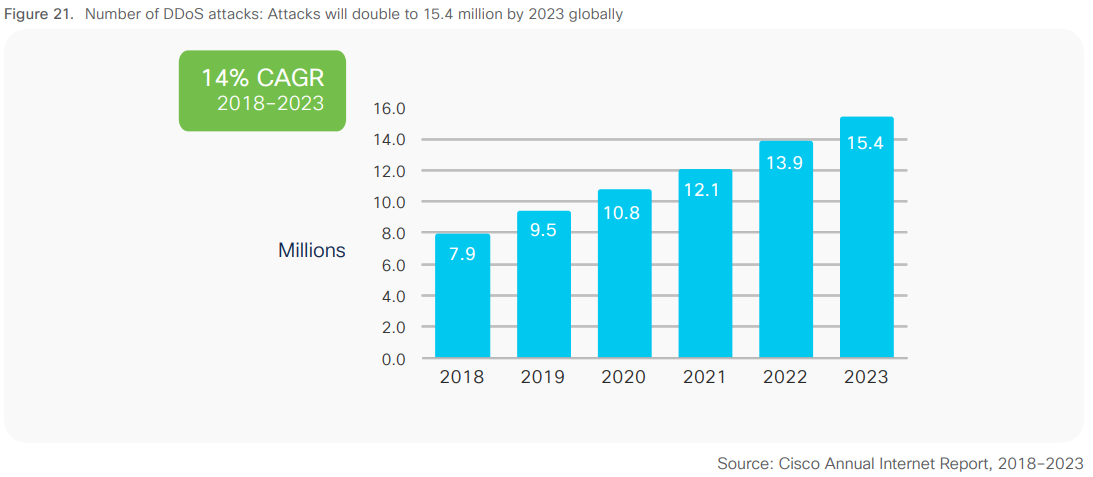
- DDoS attacks: Nearly doubled from 2018 to 2023 (Source: Cisco Annual Report).
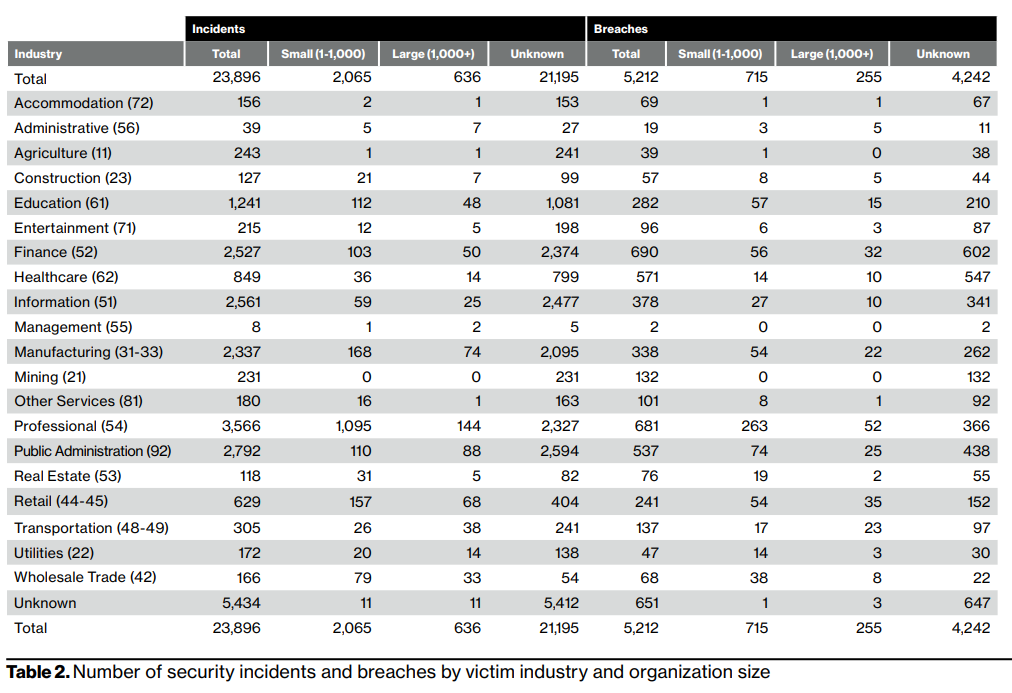
- Data Breaches: Over 5,200 confirmed breaches in 2022 alone (Source: Verizon Data Breach Investigation Report).
The chart below from Cisco Annual Report indicates that the numbers of DDoS have almost doubled from 2018 to 2023.
The Consequences of a Breach:
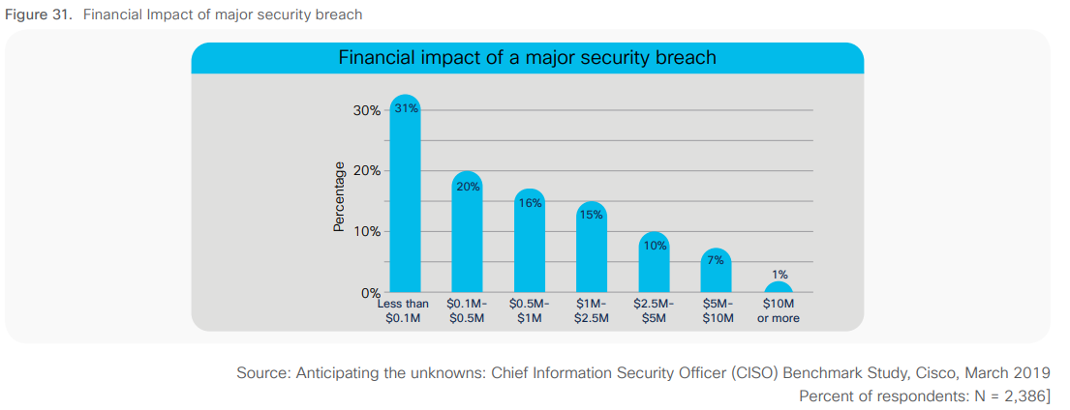
- Financial Loss: Ransom payments, remediation costs, legal fees.
- Reputational Damage: Loss of customer trust, brand erosion.
- Operational Disruption: Data loss, system downtime, productivity impacts.
- Regulatory Fines: Non-compliance penalties for data breaches.
*Incident: A security event that compromises an information asset's integrity, confidentiality, or availability.
*Breach: An incident that results in confirmed disclosure, not just potential data exposure to an unauthorized party.
Protecting Your Business
Investing in cybersecurity is crucial for protecting your business, customers, and future. Here's how we can help:
- Understanding Your Needs: We conduct a comprehensive assessment to understand your unique risks and vulnerabilities.
- Tailored Solutions: We design and implement customized cybersecurity strategies, not one-size-fits-all solutions.
- Proactive Defense: We employ advanced tools and strategies to prevent attacks before they happen.
- Continuous Monitoring: We constantly monitor your systems for suspicious activity and vulnerabilities.
- Employee Training: We empower your team with cybersecurity awareness training to minimize human error.
Benefits of Choosing Dasilva Consulting:
- Experienced & Certified: Our team holds industry-recognized cybersecurity certifications and proven expertise.
- Dedicated Partner: We prioritize ongoing support and communication to ensure your continued security.
- Cost-Effective Solutions: We tailor our services to your budget and deliver maximum value.
- Peace of Mind: Focus on your business, knowing your data and operations are protected.
Don't wait for a cyberattack to disrupt your business. Contact us today for a free consultation and let's work together to secure your future.
Don't Let These Common Vulnerabilities Bring Your Business Down:
Small businesses may be nimble and innovative, but they also face unique cybersecurity challenges. Here are five common vulnerabilities that make SMBs attractive targets and tips on how to strengthen your defenses:
1. Cybersecurity Blind Spots
Think cyber-attacks only happen to tech giants? Think again. Lack of awareness among employees about phishing scams, social engineering tactics, and online threats leaves your business wide open.
Solution: Implement ongoing cybersecurity training programs for all employees, refresh knowledge regularly, and simulate phishing attacks to test effectiveness.
2. Password Panic
Weak passwords are like open doors for cyber thieves. Don't settle for short, predictable combinations or reuse them across multiple accounts.
Solution: Enforce strong password policies (minimum length, upper/lower case, symbols, etc.) and encourage the use of password managers for enhanced security.
3. Software Stalemate
Outdated software with unpatched vulnerabilities is a hacker's paradise. Don't let these ticking time bombs compromise your security.
Solution: Make software updates a priority, automate patching whenever possible, and consider vulnerability scanning tools to identify and address risks proactively.
4. Physical Security Slip-Ups:
Unlocked workstations, unsecured Wi-Fi networks, and lax access control measures make it easy for unauthorized individuals to walk in and wreak havoc.
Solution: Implement physical security policies, secure entry points, use strong Wi-Fi passwords with WPA2 encryption, and limit physical access to sensitive information.
5. Cloud Confusion
The cloud offers great benefits, but misconfigured settings and insecure practices can turn it into a vulnerability.
Solution: Utilize dedicated accounts for each employee, enable multi-factor authentication for all cloud services, and follow best practices for securing cloud storage and applications.
Remember: Patching these vulnerabilities may seem daunting, but the consequences of ignoring them are far worse. Regular training, strong passwords, and proactive security measures are your first line of defense. Invest in cybersecurity today and build a resilient business that outpaces your competitor.
Building Your Cybersecurity Fortress: Essential Controls for SMBs
This guide outlines five critical control areas to build your cyber defenses:
1. Identify
- Critical Assets: Pinpoint your essential processes and data – maintaining secure payment portals, protecting customer information, or ensuring accurate data access.
- Information Flow: Map your data journey – understand what information you collect, where it resides, and how it flows, especially with external partners.
- Hardware & Software: Take inventory – create a simple list of your computers and software to identify potential entry points for attackers.
- Cybersecurity Policies: Establish clear guidelines – define roles, responsibilities, and expectations for protecting information and critical processes.
- Threats & Risks: Manage risk proactively – identify, assess, and document internal and external threats in a risk register, with prioritized responses and monitored results.
2. Protection
- Access Control: Grant individual user accounts and limit access to information, computers, and applications based on job requirements. Implement strong authentication (passwords, multi-factor) before access is granted. Secure physical access to devices as well.
- Data Security: Protect sensitive data with encryption at rest and in transit. Consider integrity checks to ensure authorized changes only, and securely delete data when no longer needed.
- Regular Backups: Automate backups using built-in features or software solutions. Keep one frequently saved backup offline to safeguard against ransomware.
- Device Security: Install host-based firewalls and endpoint security solutions. Manage device configurations and disable unnecessary features. Implement a secure device disposal policy.
- Vulnerability Management: Regularly update operating systems and applications to patch vulnerabilities. Consider automated updates and vulnerability scanning tools to proactively address high-risk issues.
- User Training: Regularly train and retrain employees on cybersecurity policies, procedures, and their specific roles in protecting your business.
3. Detection
- Threat Detection Technology: Combine human analysis with tools like security event, network, and endpoint threat detection to monitor your entire network for suspicious activity. Utilize threat intelligence in SIEM, antivirus, IDS, and web proxy technologies.
- Early Warning & Response: Employ real-time notifications or alerts to detect active threats and trigger pre-planned response measures to minimize damage and protect data.
4. Response
That's why having a clear and actionable incident response plan is crucial for any SMB. Here's what you need to know:
Building Your Response Team:
- Assemble your A-Team: Gather security analysts, IT managers, and relevant experts to form a dedicated incident response team. Assign clear roles and responsibilities for each member.
- Plan Your Moves: Develop a detailed incident response plan outlining steps to take for different threat scenarios. Include contact information for key team members and readily accessible playbooks for specific situations.
Responding to an Attack:
- Identify the Threat: Use monitoring tools and incident detection technology to quickly pinpoint suspicious activity. The sooner you identify, the faster you can contain the damage.
- Contain the Attack: Prioritize stopping the spread of the threat. This might involve isolating affected systems, shutting down specific services, or segmenting your network.
- Eradicate the Threat: Once contained, focus on eliminating the attacker's presence. This could involve removing malware, applying security patches, and closing any entry points exploited.
- Recover and Restore: Assess the damage and restore compromised data or systems using backups. Address any regulatory or compliance issues arising from the incident.
- Learn and Adapt: Analyze what happened and identify areas for improvement. Update your incident response plan and educate employees on lessons learned to prevent future attacks.
Remember:
- Every minute counts: Having a pre-determined plan helps your team take decisive action without wasting time in crisis.
- Communication is key: Keep stakeholders and affected employees informed throughout the process.
- Practice makes perfect: Regularly test and refine your incident response plan through simulations and training exercises.
By investing in a robust incident response plan and team, you empower your SMB to navigate cyber threats effectively and minimize the impact of potential attacks. Don't wait for a breach to become prepared - build your incident response fortress today!
5. Recovery
Picking Up the Pieces: Your SMB's Guide to Post-Breach Recovery
The dust has settled after an attack. Now what? Recovering from a cyber incident requires a strategic and well-coordinated approach. Here's how your SMB can bounce back with minimal disruption:
First Aid for Your Business:
- Assess the Damage: Evaluate the extent of the attack, identify impacted systems and data, and determine the financial and reputational consequences.
- Restore Operations: Prioritize critical business functions and bring them back online using backups and established recovery procedures. Minimize downtime and ensure essential services are operational.
- Communicate Effectively: Keep stakeholders and employees informed about the incident, the recovery process, and any necessary precautions. Transparent communication builds trust and minimizes panic.
- Protect Evidence: Secure logs, system configurations, and other forensics data to assist with investigation and potential legal proceedings.
Building a Stronger Future:
- Analyze the Root Cause: Investigate how the attack happened, identify vulnerabilities exploited, and understand the attacker's motives. This helps prevent future breaches by closing security gaps.
- Patch and Harden Systems: Apply security updates and patches to all affected systems to address vulnerabilities exposed during the attack. Strengthen your security posture by implementing additional safeguards.
- Review and Improve: Evaluate your incident response plan and identify areas for improvement. Update your playbooks, train employees on lessons learned, and consider conducting vulnerability assessments to continually bolster your defenses.
Remember:
- Recovery is a journey: While immediate restoration is crucial, long-term improvements in security infrastructure and practices are essential.
- Invest in resilience: Proactive cybersecurity investments like secure backups and a robust incident response plan minimize downtime and recovery costs.
- Learn from every incident: Each attack presents an opportunity to strengthen your defenses and build a more resilient organization.
By following these steps and prioritizing continuous improvement, your SMB can emerge from a cyber incident stronger and more prepared to face future threats. Don't let a breach define your future - transform it into a catalyst for growth and greater security!




